- Getting Started
- Use Case
- Message Type
- Sales
- Void
- Refund
- Inquiry
- Pre/Init Recurring
- Recurring
- Init Installment
- Installment
- Terminate
- PreAuth
- Sales Complete
- Message Table
- Tool
MAC Verification Process
Paydee’s MPI Server validates all the MAC (Message Authentication Code) signature it receives. Why? To ensure the payload wasn’t tampered mid transfer.
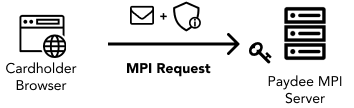
There are 3 important steps in MAC validation.
Step 1: Exchange of public RSA keys
Step 2: Generate MAC signature
Step 3: Validate MAC signature
Subsequent section will cover each step in details.
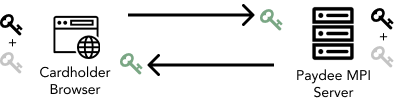
Step 1: Exchange Public Key
At the beginning of a new session, both endpoints must generate a pair of public and prive RSA keys. The public keys are then encoded and exchanged. Therefore, each endpoint get a copy of the other's public RSA key.
 |
Public RSA 2048 bit key |
 |
Private RSA 2048 bit key |
 |
Base64 Encoded Public RSA 2048 bit key
‘-’ converted to ‘+’ ‘/’ converted to ‘_’ ‘=” omitted |
Download Example
Step 2: Generate MAC signature
A MAC signature can be regarded as the encrypted value of the whole message. Below is an example of a whole message:
| Message Control | Value |
|---|---|
| MPI_TRANS_TYPE: | SALES |
| MPI_PURCH_AMT: | 100 |
| MPI_CARD_HOLDER_NAME: | TestUser |
| MPI_PAN: | 5100000000000100 |
| MPI_PAN_EXP: | 2508 |
| MPI_CVV2: | 123 |
| MPI_TRXN_ID: | txid20211018235911 |
| MPI_PURCH_DATE: | 20211018235911 |
| MPI_PURCH_CURR: | 458 |
| MPI_ADDR_MATCH: | N |
| MPI_MERC_ID: | 000000000000051 |
A MAC is generated by concatenating all the message components, hashed with SHA256 and signed with own Private RSA key.

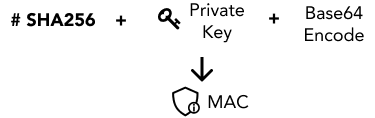
The message has to be concatenated in the right sequence. Note, there should not be any SPACEs in between the message components. The symbol "=" in the signature must be omitted too.
Download these helpful resources:
Message Concatenation Sequence MAC Sample Data
To send a message, the originating endpoint sends a message together with the MAC signature. The receiving endpoint must validate the message against the MAC signature. This ensures that message is authentic and has not been tampered with.
Step 3: Validate MAC signature
Follow these simple guides to validate a MAC signature.
i. Restore MAC signature by appending the missing ‘=’ symbol that has been omitted by the sender and decode using Base64 algorithm.

‘=” appended
+
Decode
ii. Concatenate the message received.

‘+’ converted to ‘-’
‘_’ converted to ‘/’
‘=’ appended
+
iii. Concatenate all message components received.

iv. Use OpenSSL library to load the key and verify the concatenated message against the restored MAC signature.